昨天我們學會了透過多個network node,讓OpenStack的network 功能有HA的保障,而且看到由VM到Internet的封包,會在多個Chassis(就是network node)中,綁定一個做為出口的chasssis。今天,我們再更進一步來看,在HA模式下的Floating IP又是怎麼實現。
在Network HA模式下,在OpenStack上建立與使用Floating IP與只有一個network node的情況下,指令建立出來的網路架構是完全一致的。讓我們在複習一下如何使用floating ip吧。
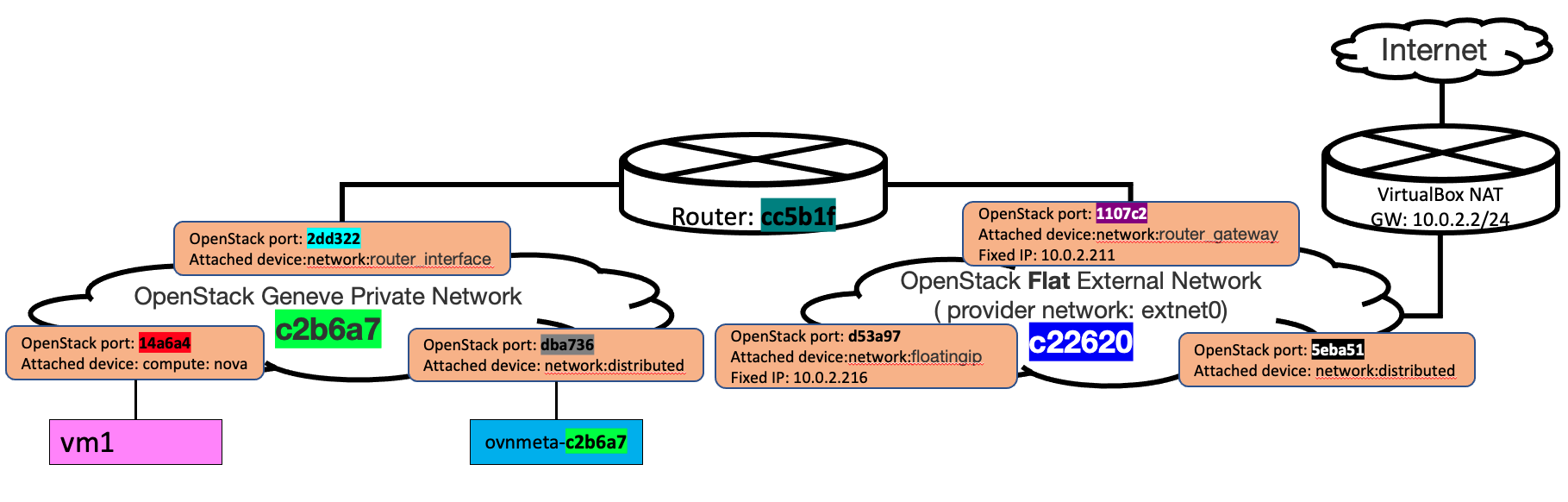
可以注意到取得的Floating IP 會屬於建立External Netwrok時,指定的 --allocation-pool之間。
openstack floating ip create ext_n2
FLOATING_IP=$(openstack floating ip list --format json | jq -rc '.[]."Floating IP Address"')
openstack server add floating ip vm_1 ${FLOATING_IP}
# Port
openstack port list --long -c ID -c "Fixed IP Addresses" -c "Device Owner" | abbrev
+--------+-------------------------------------------------+--------------------------+
| ID | Fixed IP Addresses | Device Owner |
+--------+-------------------------------------------------+--------------------------+
| 0bece6 | ip_address='172.16.100.10' , subnet_id='ec52a9' | compute:nova |
| 06ff4f | ip_address='172.16.100.2' , subnet_id='ec52a9' | network:distributed |
| 1c52f2 | ip_address='172.16.100.1' , subnet_id='ec52a9' | network:router_interface |
| e70e83 | | network:distributed |
| 268c32 | ip_address='10.0.2.211' , subnet_id='6f6c62' | network:router_gateway |
| cbae0e | ip_address='10.0.2.216' , subnet_id='6f6c62' | network:floatingip |
+--------+-------------------------------------------------+--------------------------+
要使用Floating IP存取VM時,必需建立security group設定允許的rule。實驗環境已經事先建立一個允許ICMP與SSH的sg,直接將其套用至vm上。如果沒有相對應的sg,外部會無法進行連線。
# show the pre-created sg
openstack security group show allow-icmp-ssh
# add sg to instances
openstack server add security group vm_1 allow-icmp-ssh
一旦建立floating IP後,在logical router上就會多一個DNAT的屬性,和Day-22: VM 的 Flaoting IP的差別,只在於lrp-1107c2的gateway-chassis屬性,有二個chassis id,而之前只有一個chassis id。這個特性和昨天介紹 Network 的HA的行為也是完全相同的。
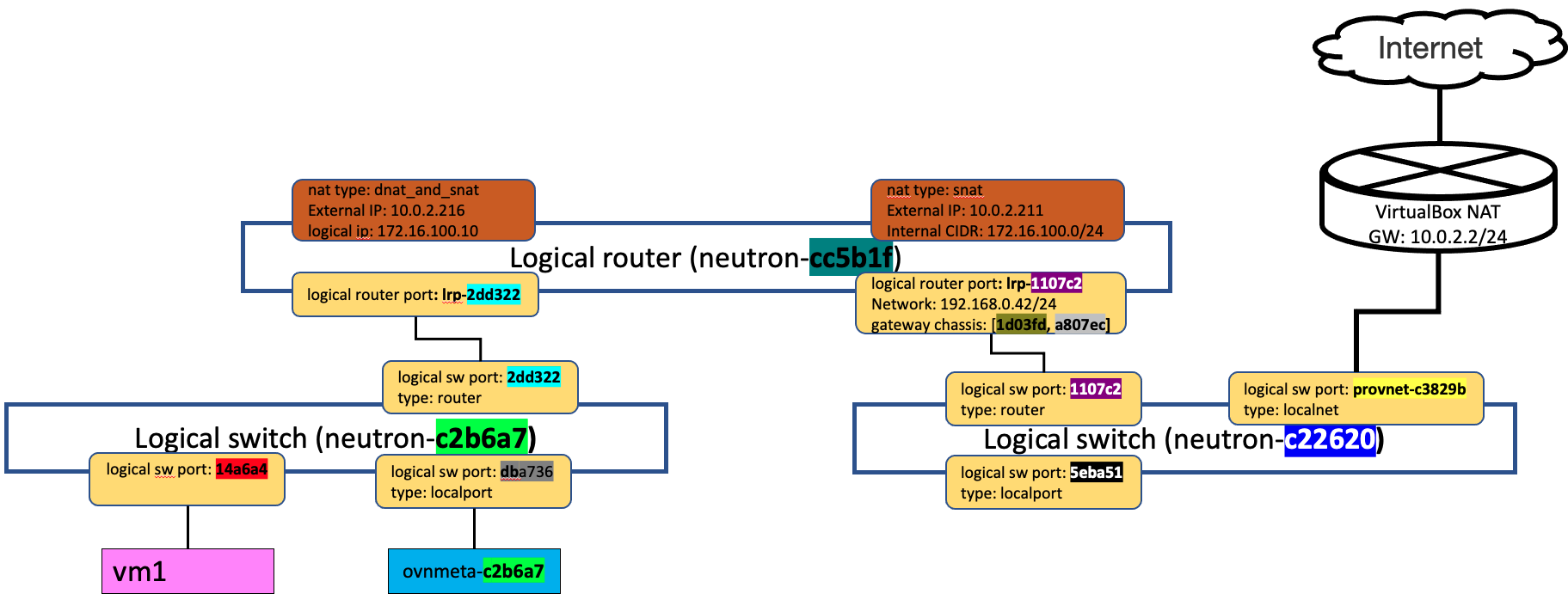
我們今天就只驗證透過flaoting IP連到 VM, 至於 由VM連到Internet的部份,大家可以依之前的操作自行驗證。
再次提醒,因為我們實驗環境的VM對外的eth0,是透過VirtualBox的NAT網路實現的,所以要驗證能否透過floating ip連到VM,一定要在network node測試。之前因為只有一個network node,所以沒什麼問題。今天有二個network node,必需先找到logical router綁定要使用network node,在上面才能透過floating ip連到VM。
ping 10.0.2.216,雖然是要連到10.0.2.216,但在geneve tunnel上,會發現已經透過DNAT換成要送給172.16.100.10。tcpdump -vvneei eth1 'udp port 6081'
03:52:14.742209 52:54:00:82:23:6d > 52:54:00:ea:65:ed, ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 64, id 39673, offset 0, flags [DF], proto UDP (17), length 142)
192.168.33.10.47005 > 192.168.33.30.geneve: [bad udp cksum 0xc3fa -> 0x7024!] Geneve, Flags [C], vni 0x1, proto TEB (0x6558), options [class Open Virtual Networking (OVN) (0x102) type 0x80(C) len 8 data 00030002]
fa:16:3e:d0:74:be > fa:16:3e:3c:24:6e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 12034, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.2.15 > 172.16.100.10: ICMP echo request, id 1, seq 1, length 64
03:52:14.744315 52:54:00:ea:65:ed > 52:54:00:82:23:6d, ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 64, id 52973, offset 0, flags [DF], proto UDP (17), length 142)
192.168.33.30.5380 > 192.168.33.10.geneve: [bad udp cksum 0xc3fa -> 0x1825!] Geneve, Flags [C], vni 0x3, proto TEB (0x6558), options [class Open Virtual Networking (OVN) (0x102) type 0x80(C) len 8 data 00030002]
fa:16:3e:84:56:22 > de:0d:fe:eb:97:48, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 48875, offset 0, flags [none], proto ICMP (1), length 84)
172.16.100.10 > 10.0.2.15: ICMP echo reply, id 1, seq 1, length 64
在compute上,會收到透過geneve tunnel由network-controller送過來的 ICMP request;之後,由geneve tunnel 送ICMP reply 回給network-controller。
tcpdump -vvneei eth1 'udp port 6081'
03:52:14.742622 52:54:00:82:23:6d > 52:54:00:ea:65:ed, ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 64, id 39673, offset 0, flags [DF], proto UDP (17), length 142)
192.168.33.10.47005 > 192.168.33.30.geneve: [bad udp cksum 0xc3fa -> 0x7024!] Geneve, Flags [C], vni 0x1, proto TEB (0x6558), options [class Open Virtual Networking (OVN) (0x102) type 0x80(C) len 8 data 00030002]
fa:16:3e:d0:74:be > fa:16:3e:3c:24:6e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 12034, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.2.15 > 172.16.100.10: ICMP echo request, id 1, seq 1, length 64
03:52:14.744384 52:54:00:ea:65:ed > 52:54:00:82:23:6d, ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 64, id 52973, offset 0, flags [DF], proto UDP (17), length 142)
192.168.33.30.5380 > 192.168.33.10.geneve: [bad udp cksum 0xc3fa -> 0x1825!] Geneve, Flags [C], vni 0x3, proto TEB (0x6558), options [class Open Virtual Networking (OVN) (0x102) type 0x80(C) len 8 data 00030002]
fa:16:3e:84:56:22 > de:0d:fe:eb:97:48, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 63, id 48875, offset 0, flags [none], proto ICMP (1), length 84)
172.16.100.10 > 10.0.2.15: ICMP echo reply, id 1, seq 1, length 64
和 昨天一樣,我們也可以透過iptable 模擬network node 故障,這個時候,就必需移動到另一台network node上,透過floating IP 連線到VM。這部份也讓大家練習看看。
看完這二天對Network HA的介紹,是不是有一種感覺就是,之前在只有單一的network node的行為,基本上就只是HA模式的特例。在只有一個network node的情況下,logical router只能綁定到唯一的network node,當有多個network node時,會自動綁定到priority高的node。因為OVN本身的設計上就支援HA的架構,只要有多個network node時,就自動啟動HA的功能,也不需要做額外的設定,是不是很方便呢?
